pfSense & Azure - Set up S2S VPN with static or dynamic routing
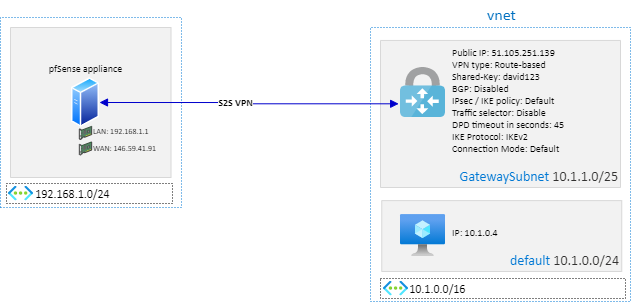
In this article, I will describe how to configure pfSense to create a S2S VPN to Azure with static or dynamic routing.
pfSense
pfSense is a free firewall/router computer software distribution based on FreeBSD. The open source pfSense Community Edition (CE) and pfSense Plus is installed on a physical computer or a virtual machine to make a dedicated firewall/router for a network. It can be configured and upgraded through a web-based interface, and requires no knowledge of the underlying FreeBSD system to manage.
Azure & pfSense - S2S VPN static souting
The pfSense configuration described in this article is based on the following architecture:

If you have not installed pfSense already, follow this tutorial to do it.
Before configuring pfSense, let’s deploy basic Azure infrastructure.
Azure infrastructure
In a resource group, create :
- A virtual Network (VNet)
- Name: vnet
- Address Space: 10.1.0.0/16
- Subnets
- default: 10.1.0.0/24
- GatewaySubnet: 10.1.1.0/25
- A virtual network gateway:
- Name: vnetgw01
- Region: same VNet location
- Gateway type: VPN
- VPN type: Route-based
- SKU: Basic
- Generation: Generation2
- Virtual network: VNet
- Public IP address name: vnetgwpip01
- Enable active-active mode: Disabled
- Configure BGP: disabled
- A local network gateway:
- Name: vnetgwlng01
- Region: same VNet region
- IP address: pfSense machine public IP (WAN interface in the schema)
- Address space: 192.168.1.0/24 (or all address space you want to route through the tunnel)
- Configure BGP settings: No
- A VNet gateway connection:
- Name: azure-to-onprem
- Connection type: Site-to-site (IPsec)
- First virtual network gateway: vnetgw01
- Local network gateway: vnetgwlng01
- Shared key (PSK): david123
- IKE protocol: IKEv2
Let’s now configure pfSense.
pfSense configuration
Create a new IPsec VPN
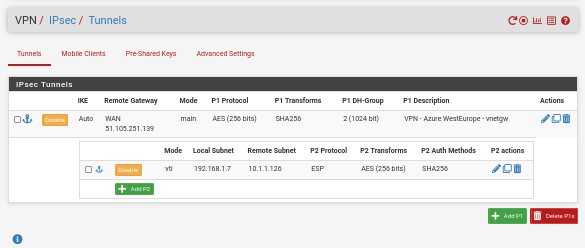
Go to VPN -> IPsec and create a new IPsec VPN:
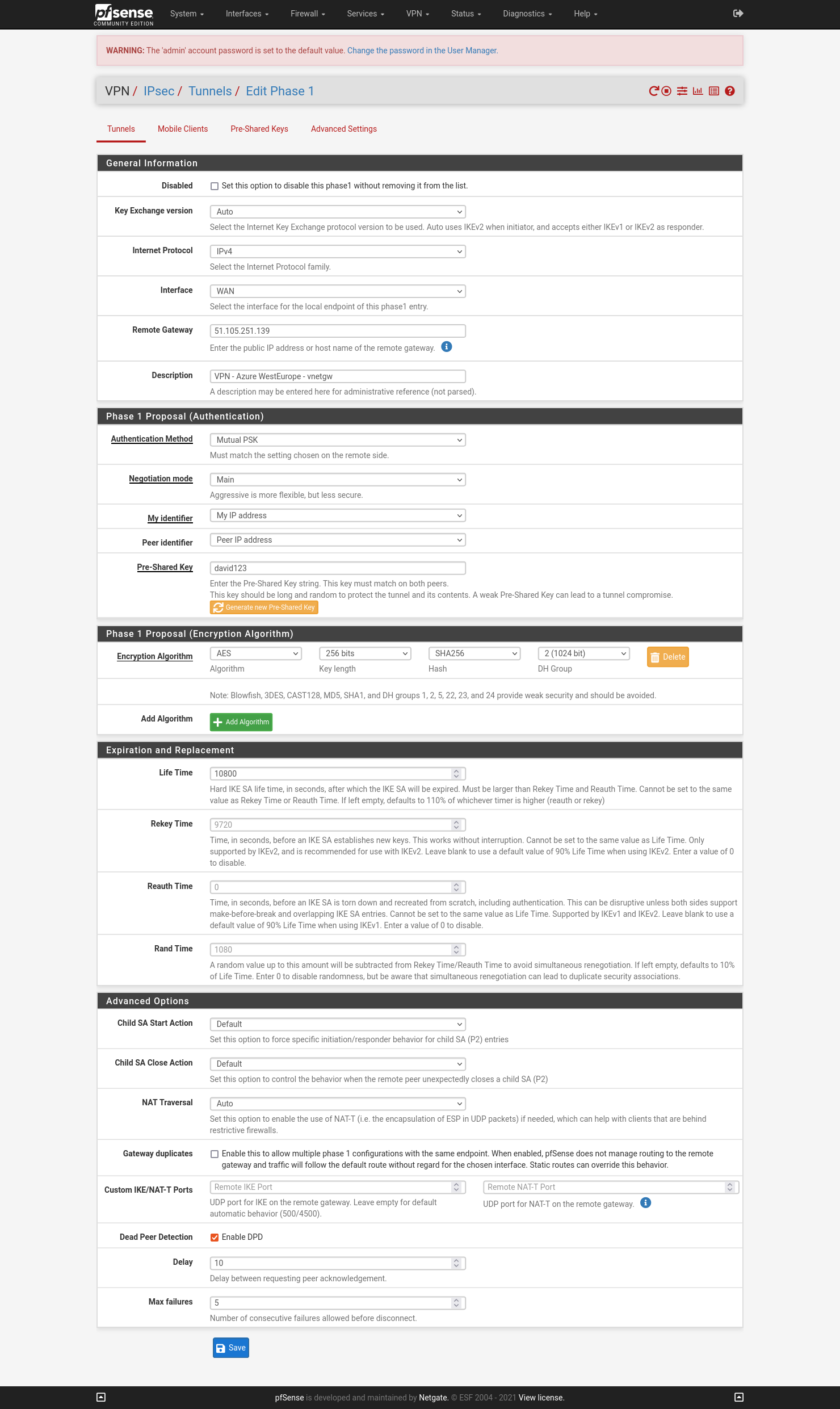
Save and apply changes.
Configure now Phase 2:
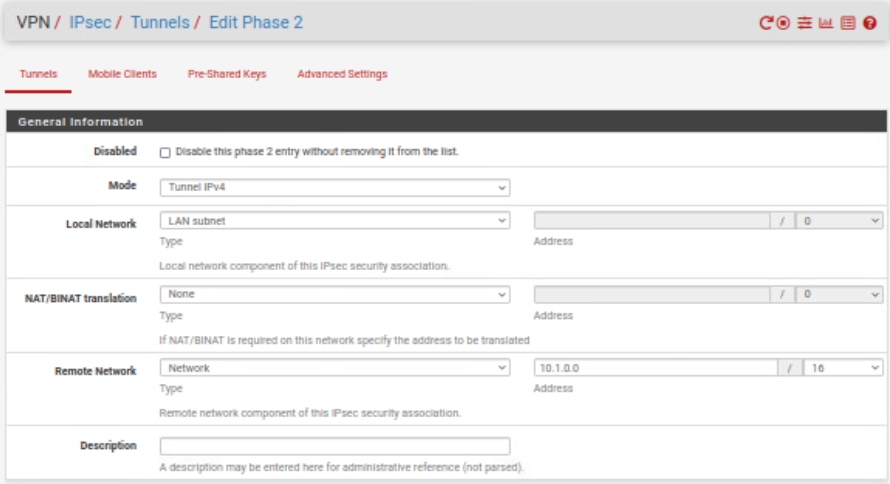
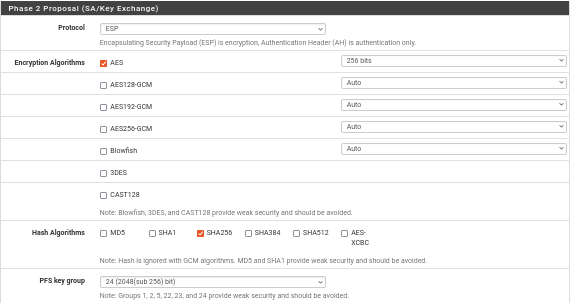
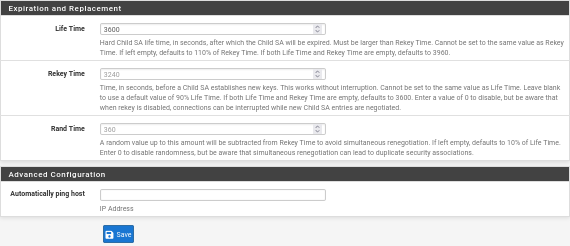
Update Phase 2 SA/Key Exchange parameters:
Do not change other parameters:
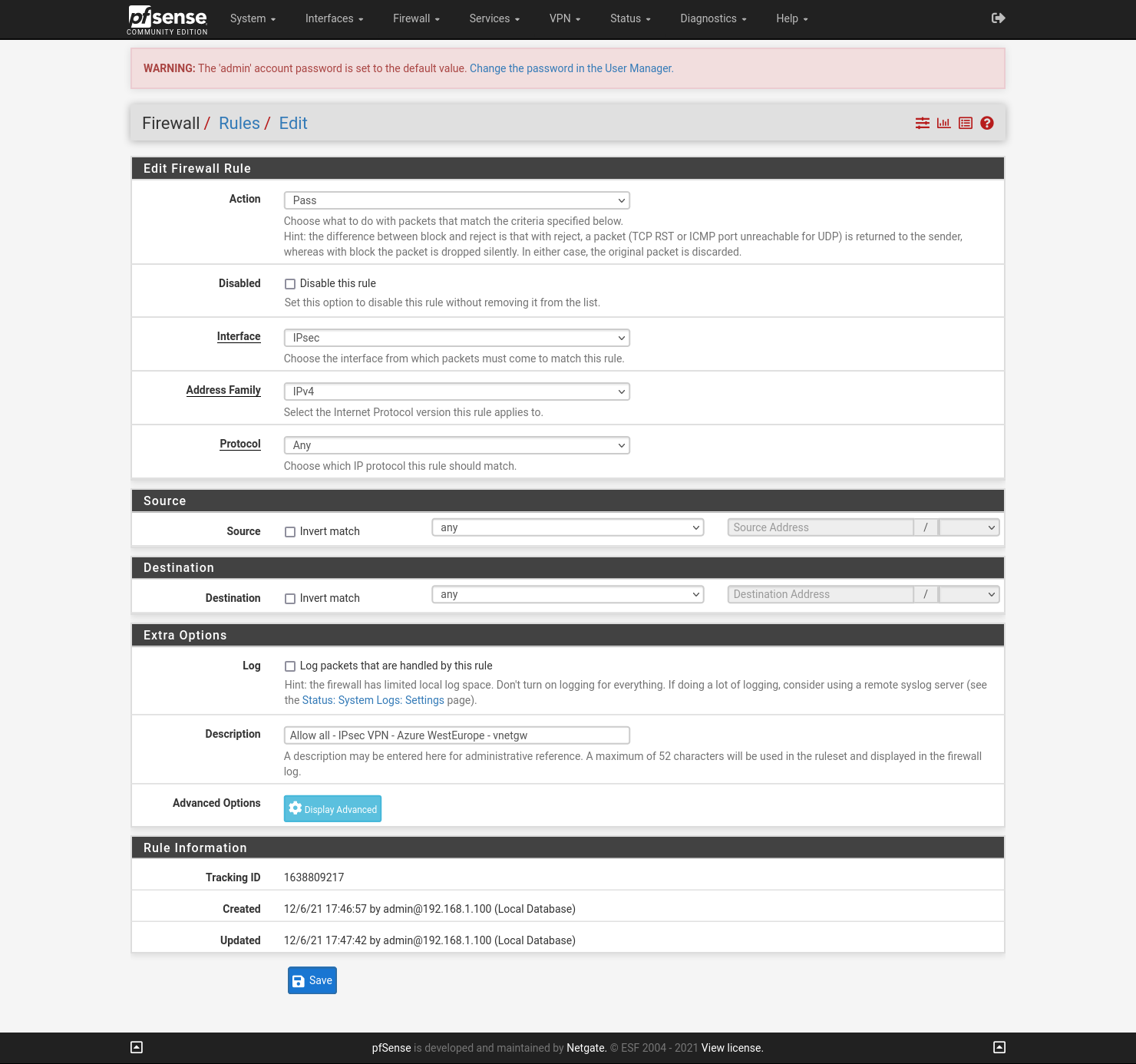
Configure IPsec Firewall rules
Go to Firewall -> Rules -> IPsec and create a new rule that will allow everything:
Save the rule and apply changes:
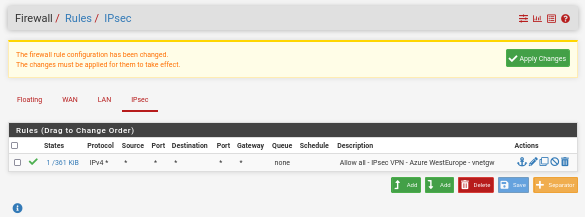
Go to Status -> IPsec:
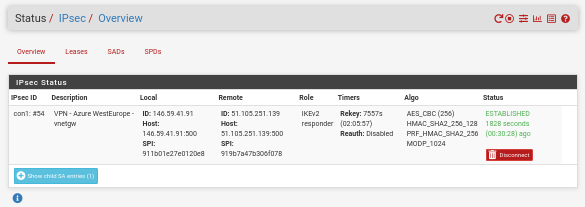
Check the VPN is connected on Azure side also:
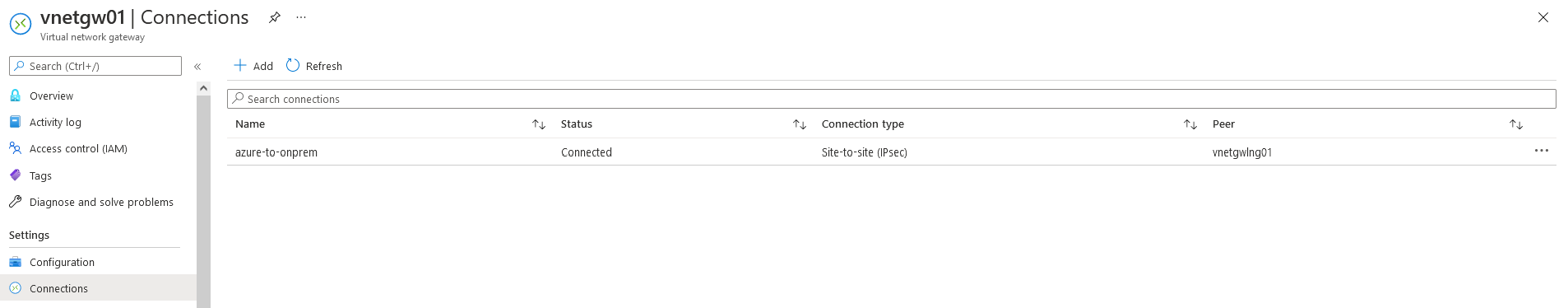
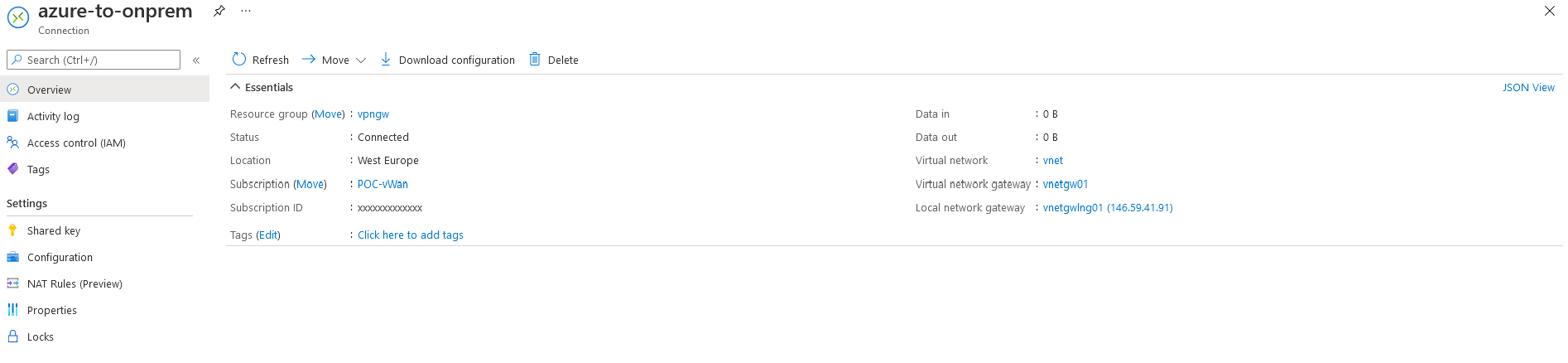
Run final connectivity checks
Provision a VM on default subnet.
Check effective routes on the network interface card:
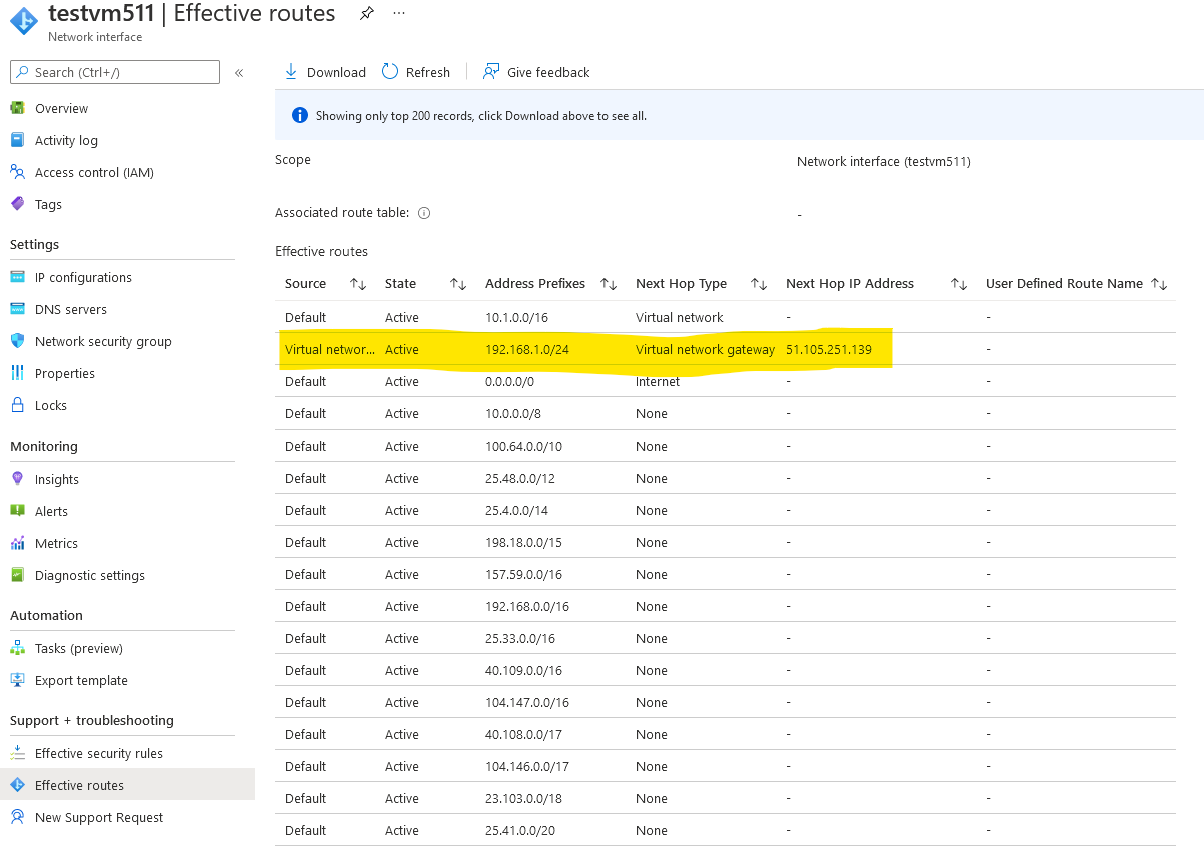
Go to Diagnostics -> Ping and ping this VM (10.1.0.4) from pfSense using LAN source address:
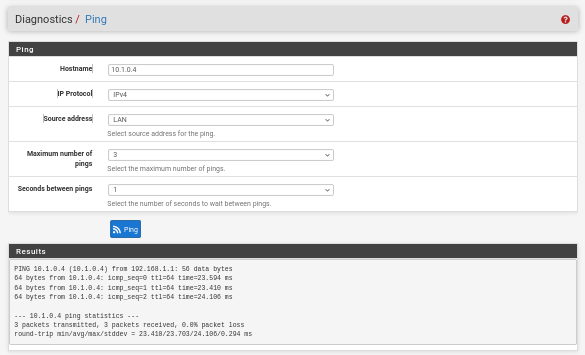
The S2S VPN between Azure & pfSense is up using static routing.
Azure & pfSense - S2S VPN dynamic routing
Azure infrastructure
I will keep the same infrastructure used previously. It is just required to update the virtual network gateway, the local network gateway and the connection.
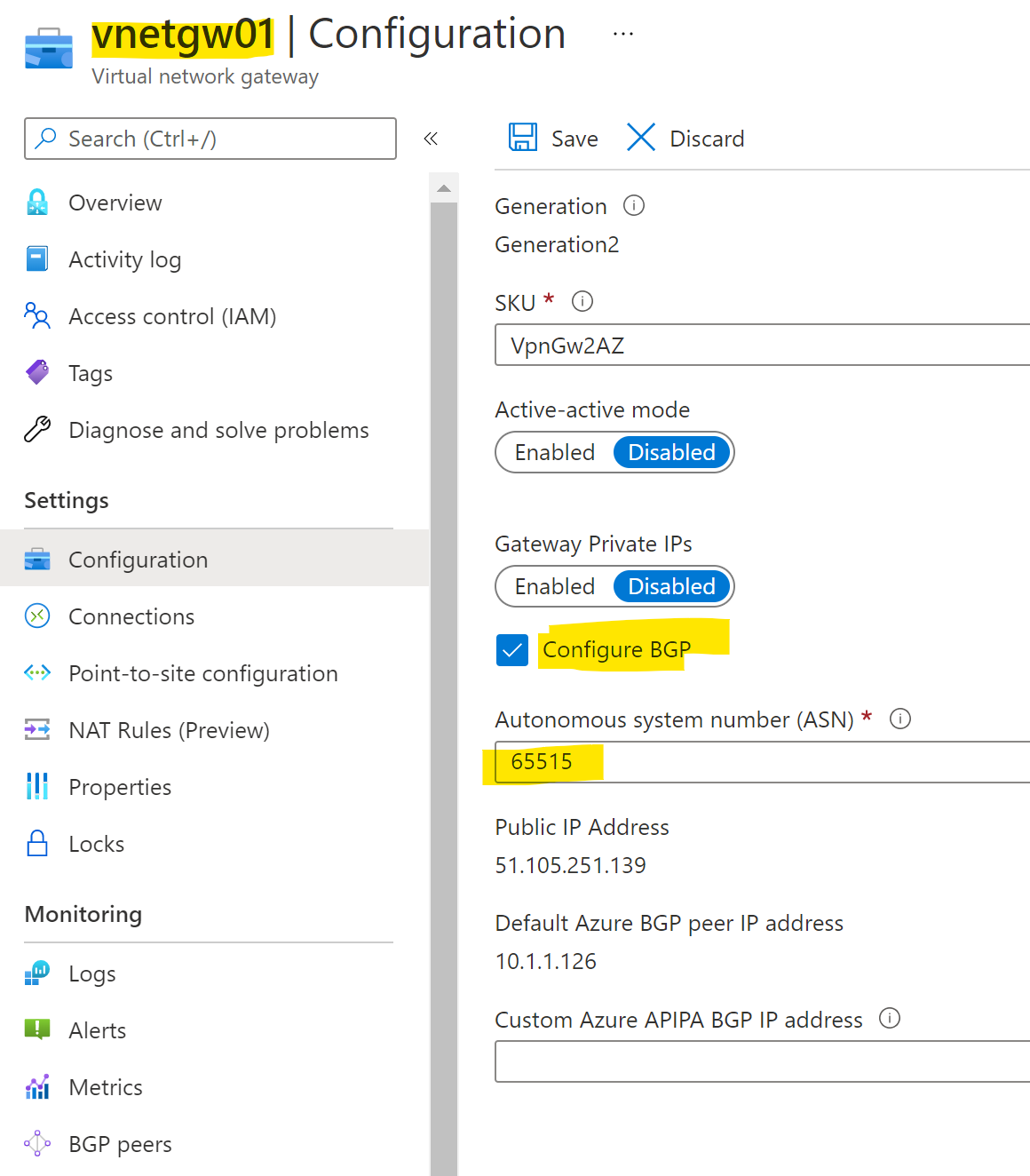
Update virtual network gateway, enable BGP and provide Azure BGP ASN:
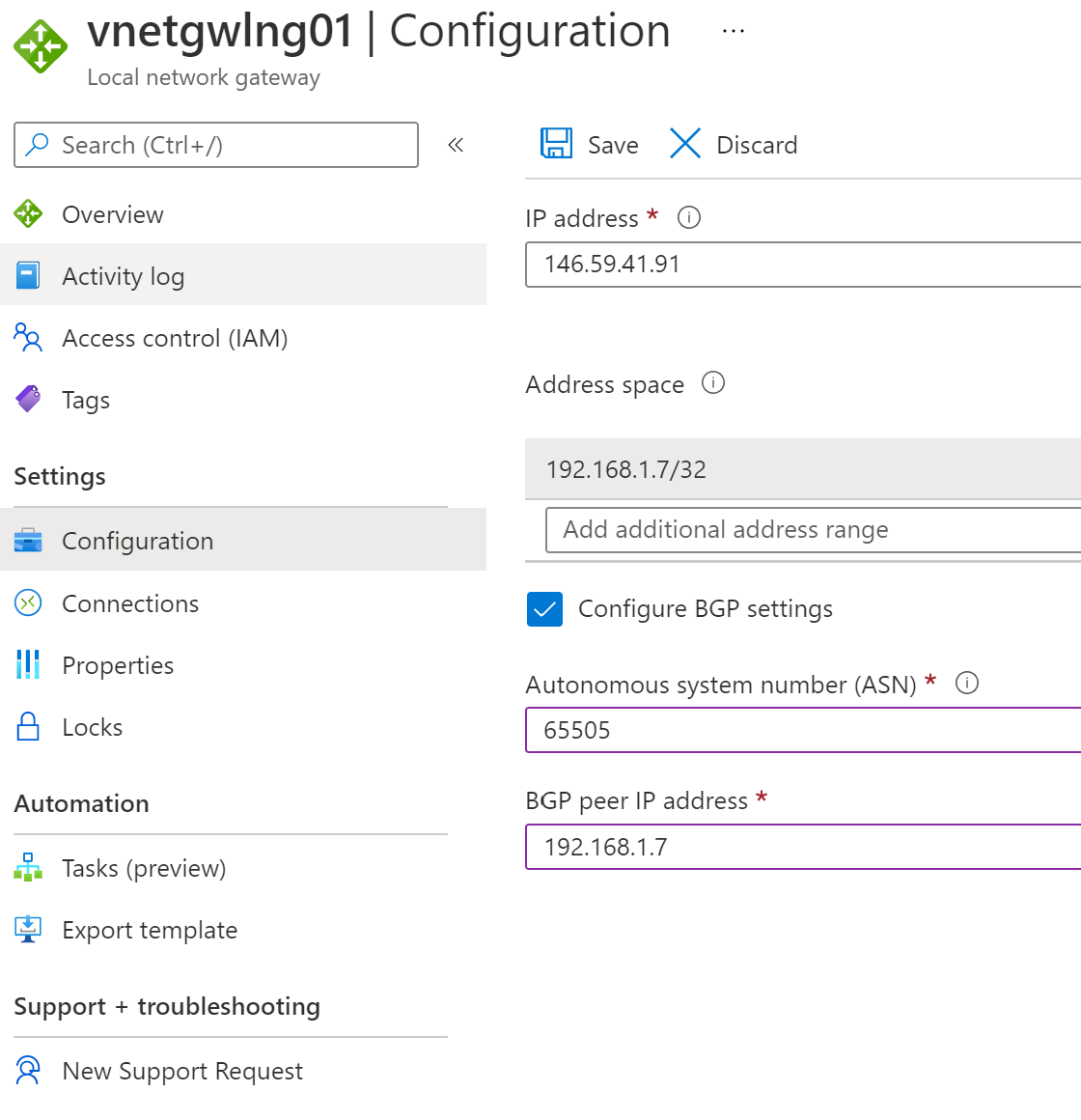
Update local network gateway, enable BGP and provide custom BGP ASN and BGP peer IP address:
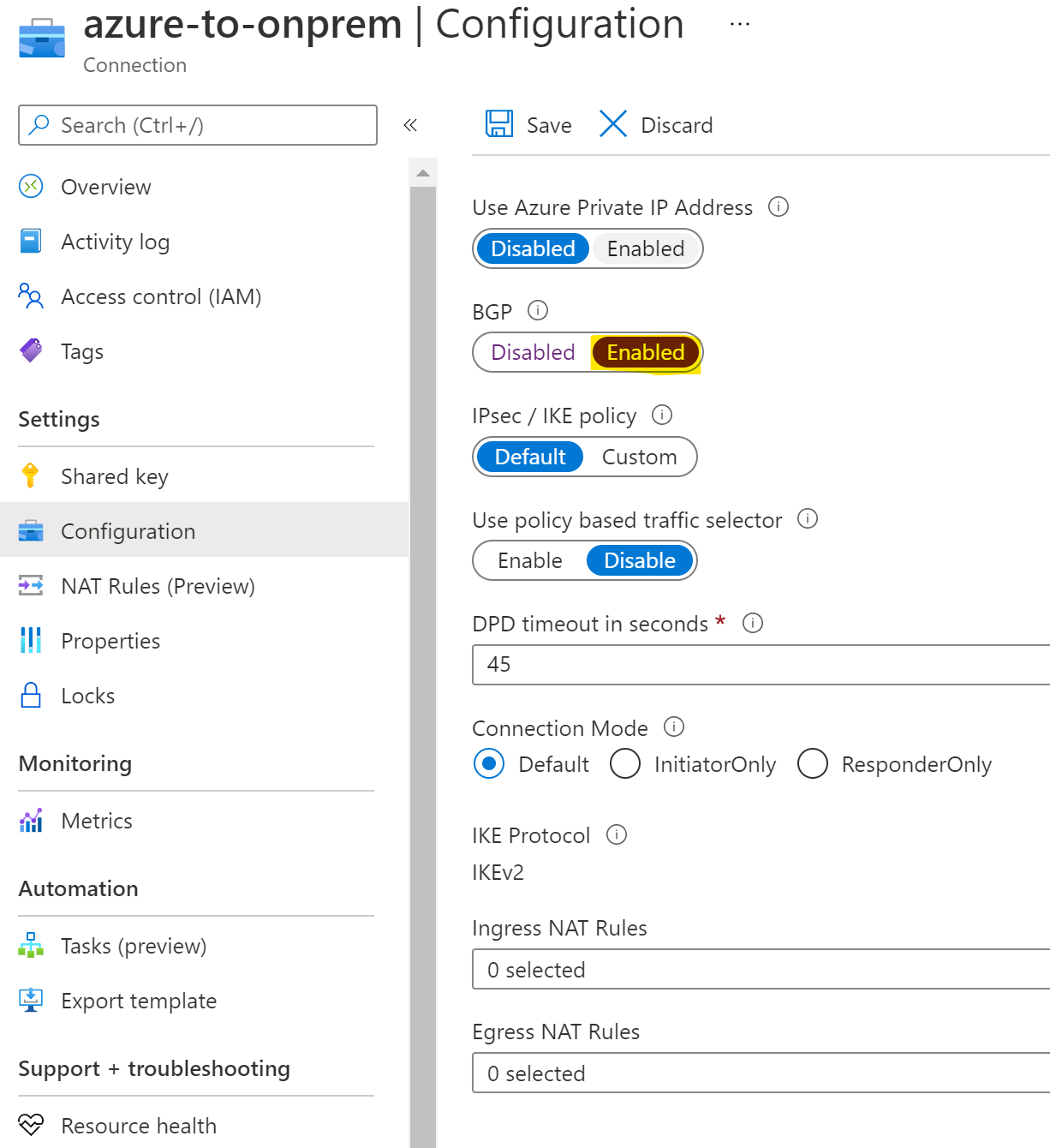
Finally, update virtual network gateway and enable BGP:
pfSense configuration
Let’s update IPsec Phase 2 configuration, install and configure FRR.
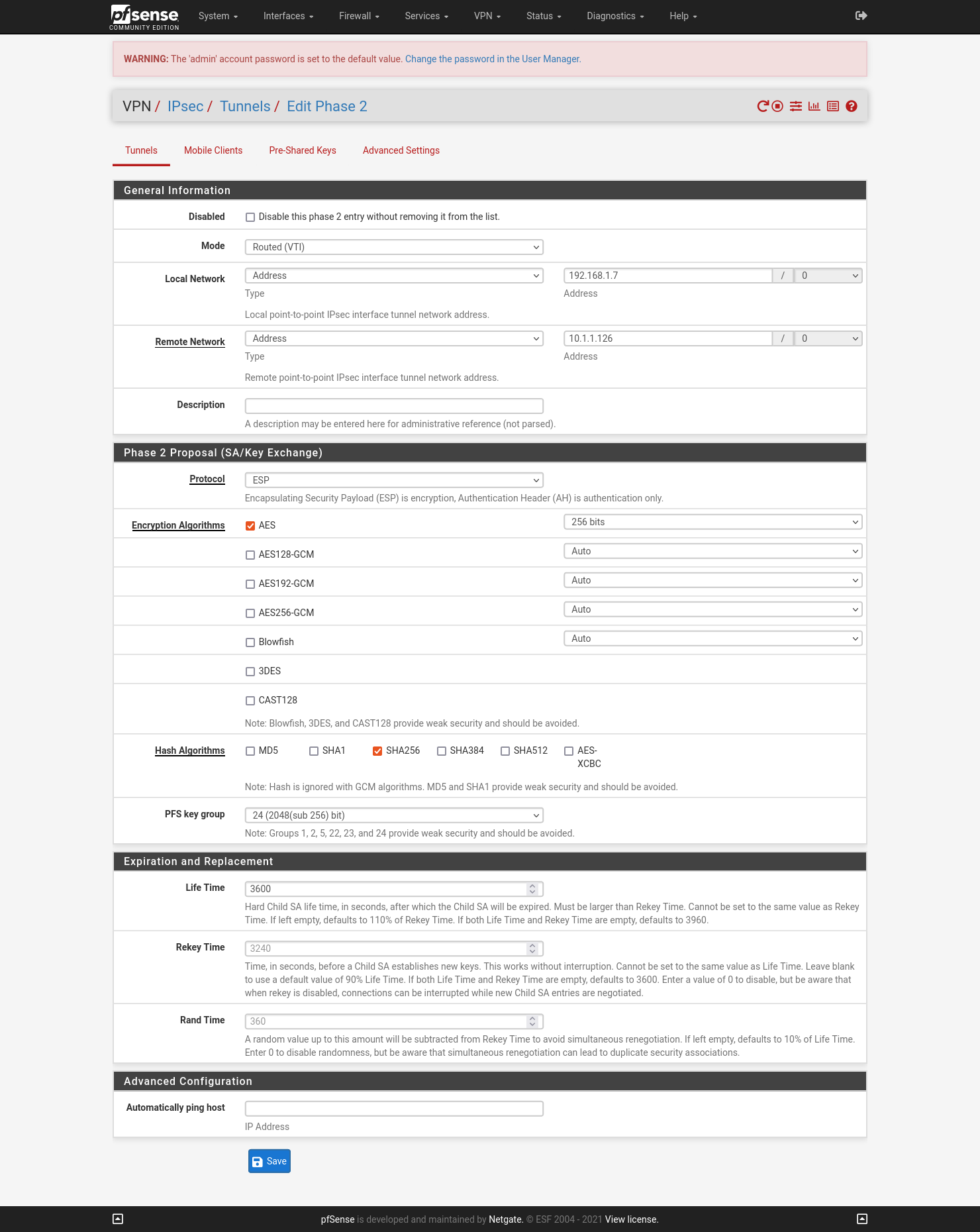
Update IPsec Phase 2 configuration
Go to VPN -> IPsec and edit IPsec Phase 2 configuration:
Install FRR package
Go to System -> Package Manager and install FRR package:
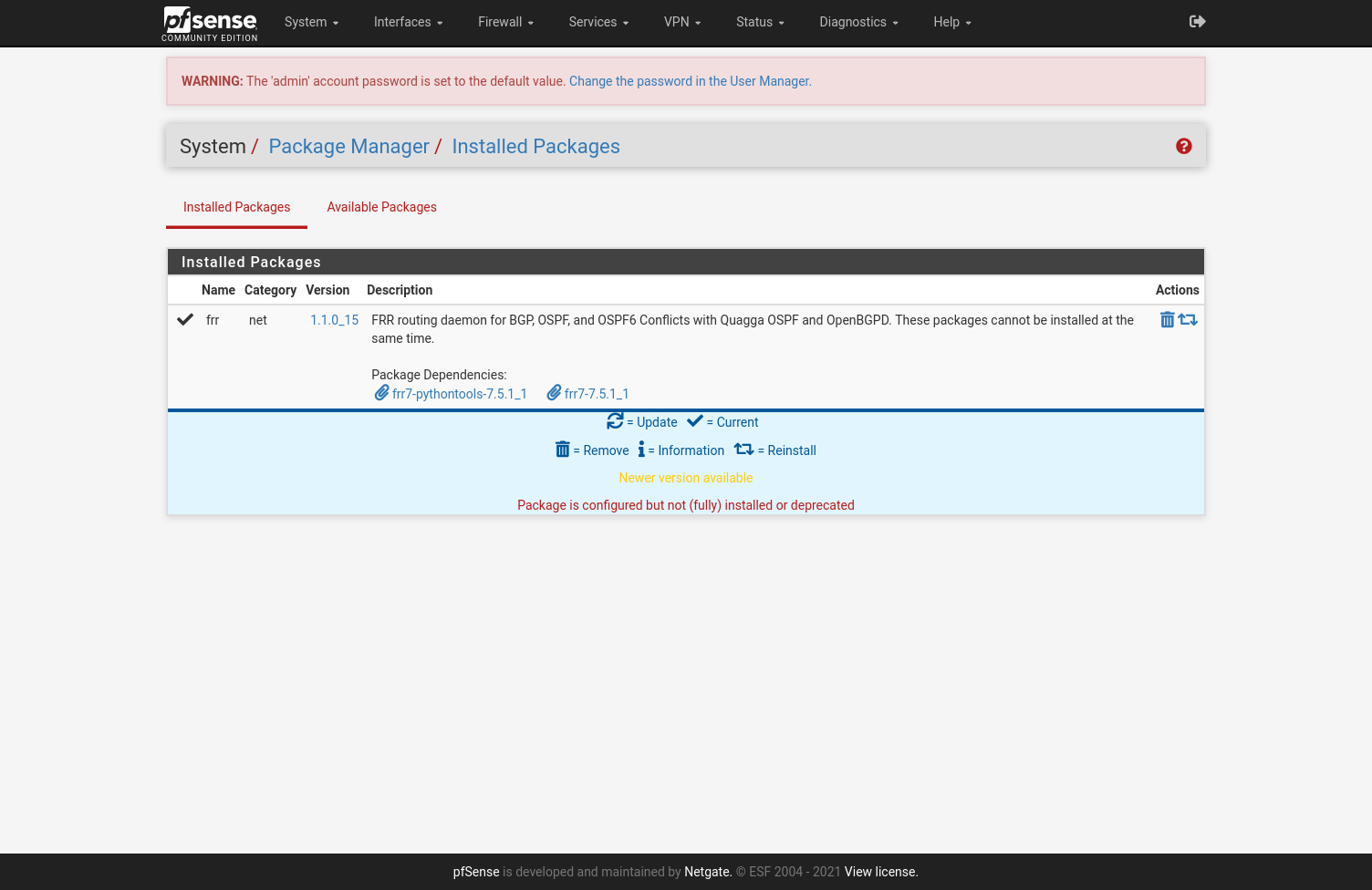
FRR package will bring BGP feature to pfSense.
Update FRR configuration
Go to Services -> FRR Global/Zebra -> Raw Config :
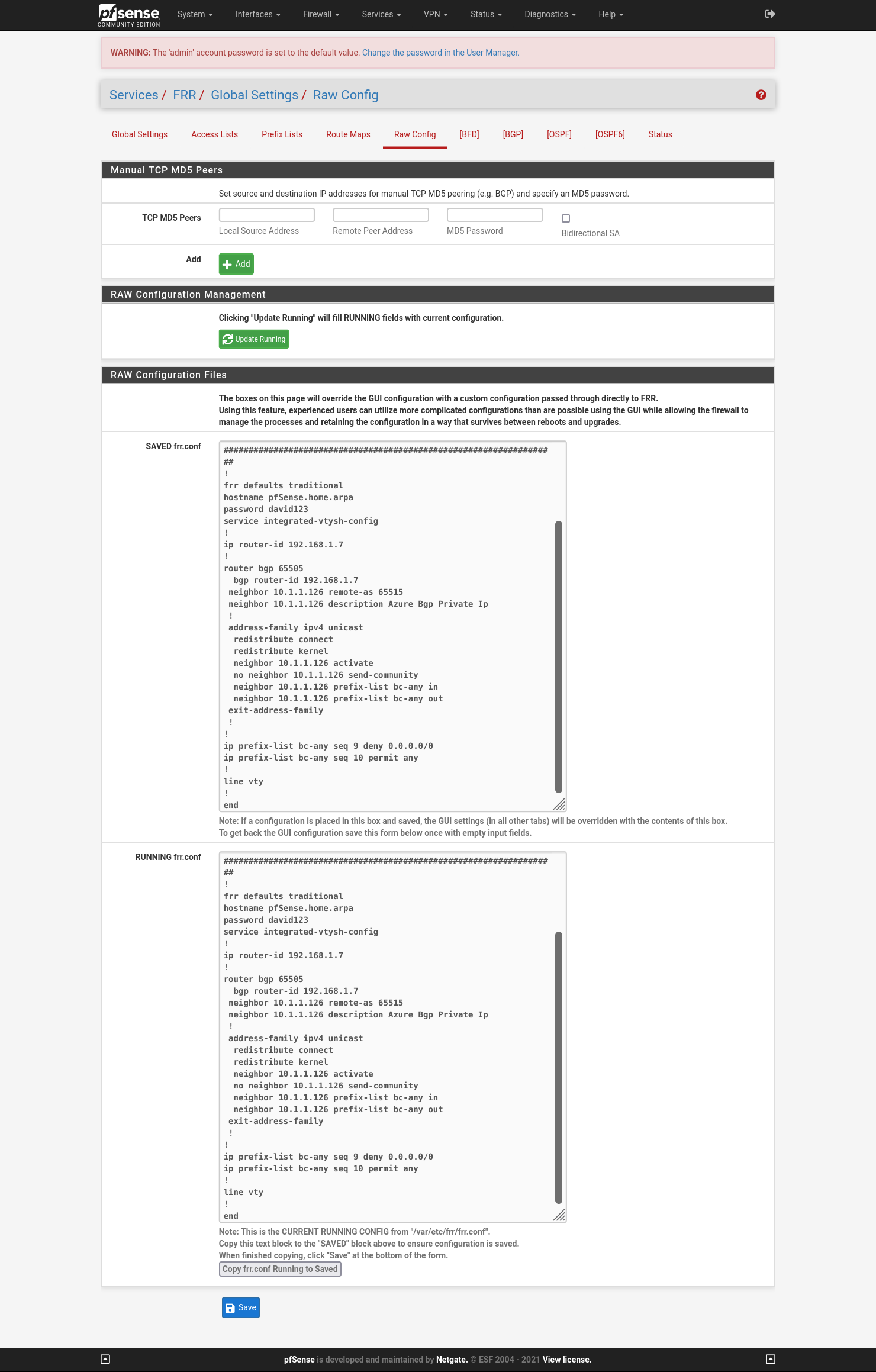
Deploy this configuration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
##################### DO NOT EDIT THIS FILE! ######################
###################################################################
# This file was created by an automatic configuration generator. #
# The contents of this file will be overwritten without warning! #
###################################################################
!
frr defaults traditional
hostname pfSense.home.arpa
password david123
service integrated-vtysh-config
!
ip router-id 192.168.1.7
!
router bgp 65505
bgp router-id 192.168.1.7
neighbor 10.1.1.126 remote-as 65515
neighbor 10.1.1.126 description Azure Bgp Private Ip
!
address-family ipv4 unicast
redistribute connect
redistribute kernel
neighbor 10.1.1.126 activate
no neighbor 10.1.1.126 send-community
neighbor 10.1.1.126 prefix-list bc-any in
neighbor 10.1.1.126 prefix-list bc-any out
exit-address-family
!
!
ip prefix-list bc-any seq 9 deny 0.0.0.0/0
ip prefix-list bc-any seq 10 permit any
!
line vty
!
Note: pfSense won’t announce 0.0.0.0/0 route with this configuration.
Save, go to Services -> FRR Gobal/Zebra -> Global Settings and Force FRR Service Restart.
Run checks
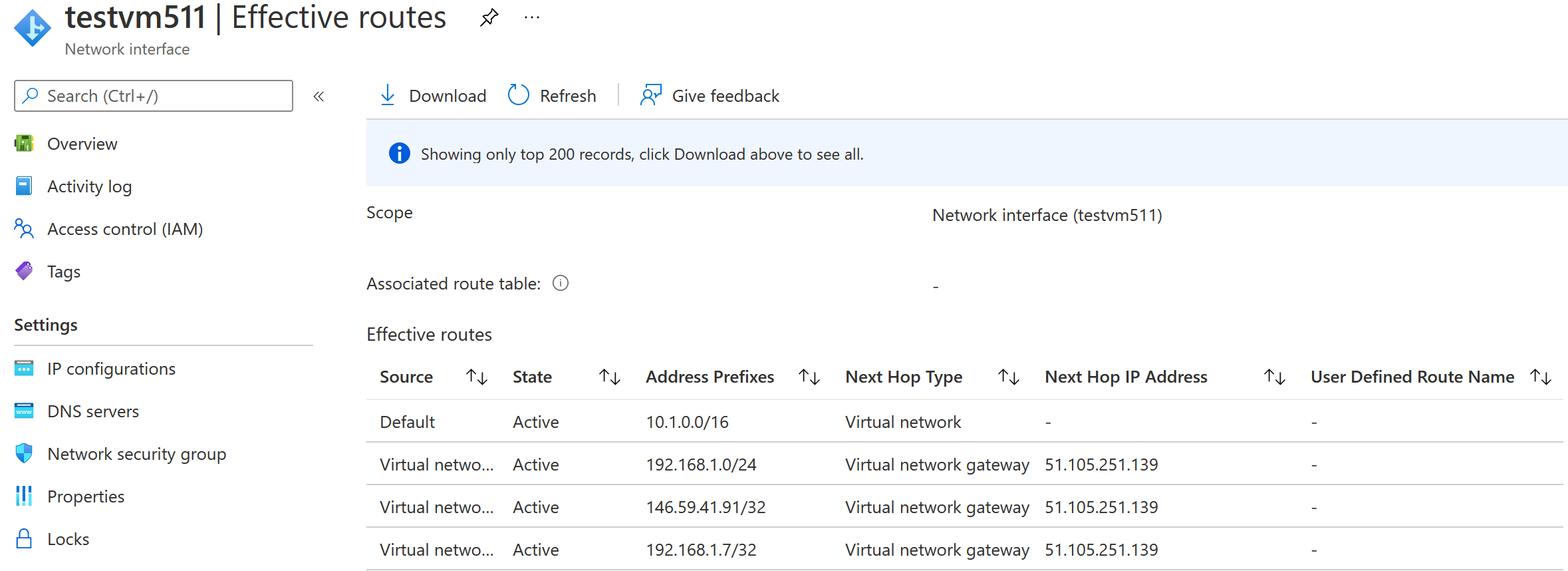
From Azure Portal, display VmTest NIC effective routes:
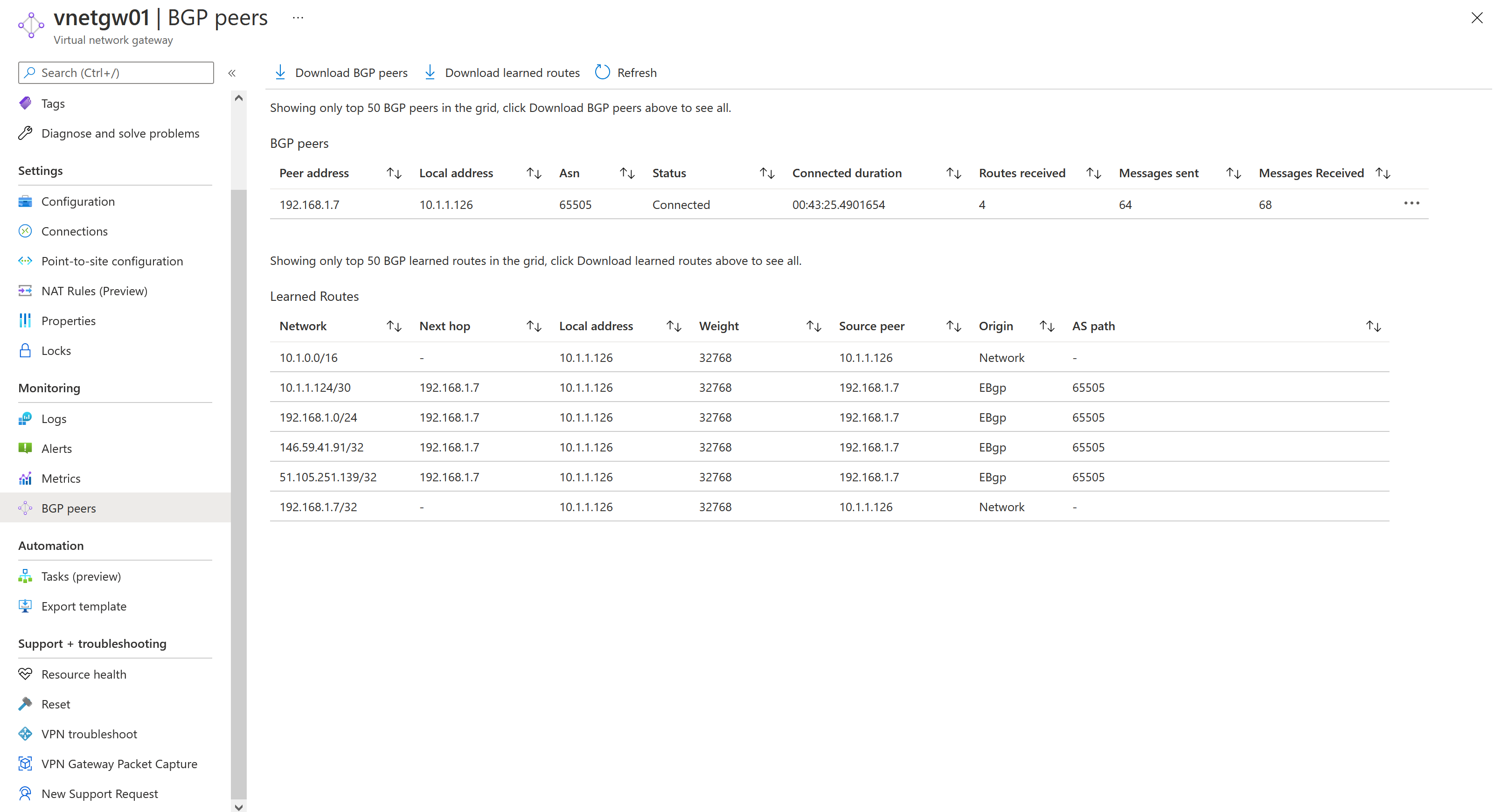
From Azure Portal, display virtual network gateway BGP peers :
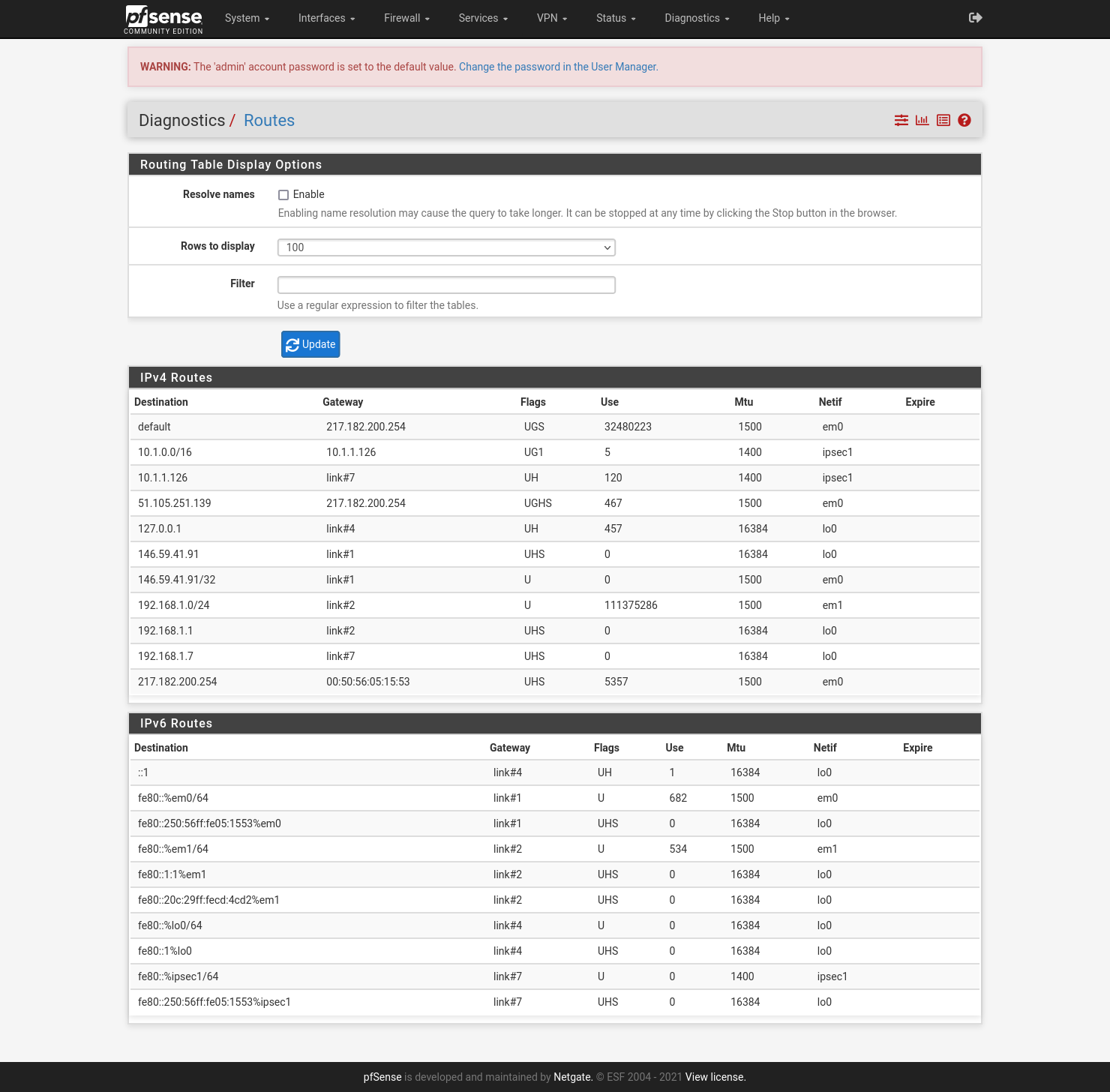
From pfSense, go to Diagnostics -> Routes:
From pfSense, go to Status -> FRR -> BGP:
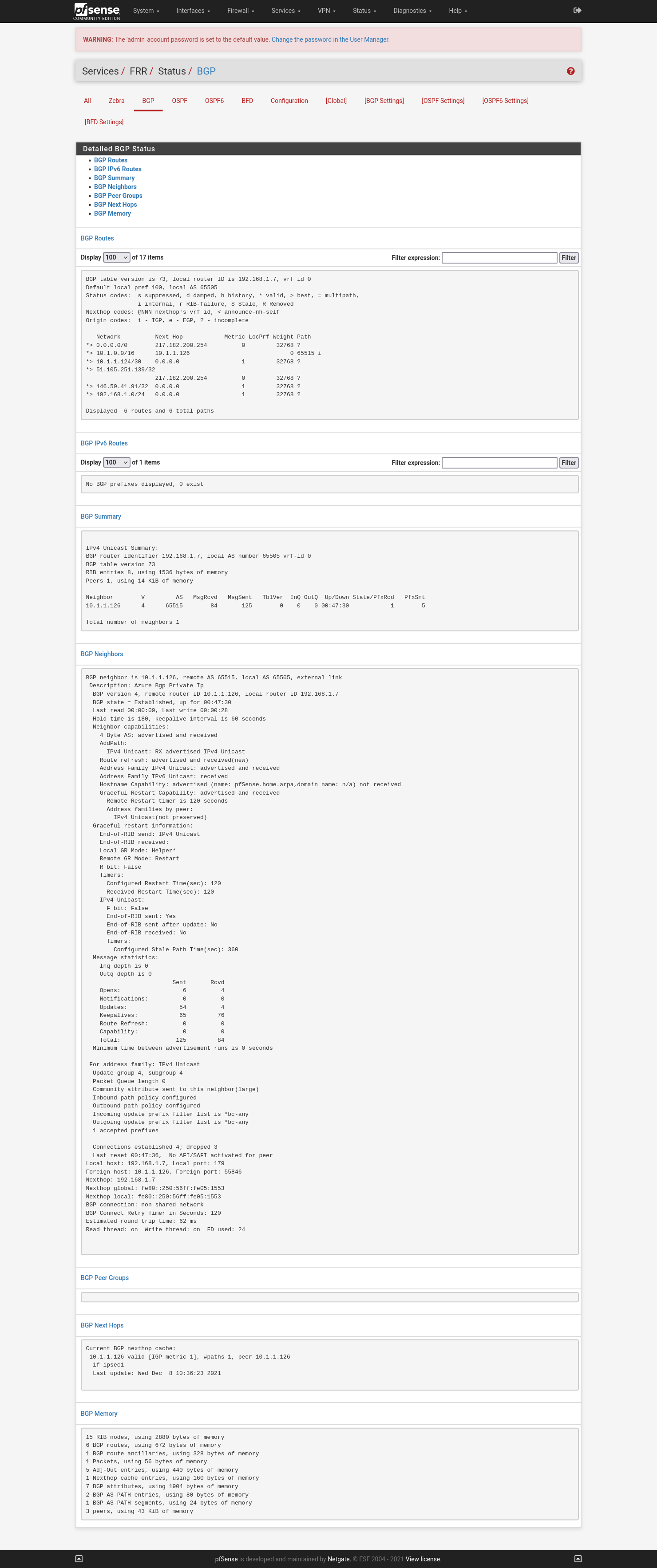
The S2S VPN between Azure & pfSense is up using dynamic routing.
References
Below articles were used to write this article (thanks authors!):
