Azure App Service (Linux&PHP) — Fix (securityheaders.com) missing HTTP Response Headers
This post was originally published on Medium.
This blog post explains how to fix headers anomalies given by securityheaders.io on Azure App Service with Linux & PHP context.
Step1 - Create the startup script for PHP
Unfortunately, we cannot use a web.config file when App Service is running Linux & Apache (normal: there is no IIS).
We need to create a shell script which will be executed when the container starts.
This shell script will modify the apache configuration for Headers service.
Upload bellow script to /home/site/wwwroot/ folder:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
#!/usr/bin/env bash
a2enmod headers
# Remove X-Powered-By
echo "Header always unset \"X-Powered-By\"" >> /etc/apache2/apache2.conf
echo "Header unset \"X-Powered-By\"" >> /etc/apache2/apache2.conf
# Strict-Transport-Security
echo "Header always set Strict-Transport-Security \"max-age=31536000; includeSubDomains\"" >> /etc/apache2/apache2.conf
# Content-Security-Policy
echo "Header set Content-Security-Policy \"default-src 'self' *.MYDOMAIN.com\"" >> /etc/apache2/apache2.conf
# Referrer-Policy
echo "Header set Referrer-Policy \"no-referrer-when-downgrade\"" >> /etc/apache2/apache2.conf
# X-Frame-Options
echo "Header set X-Frame-Options \"sameorigin\"" >> /etc/apache2/apache2.conf
# X-Frame-Options
echo "Header set X-Content-Type-Options \"nosniff\"" >> /etc/apache2/apache2.conf
# X-XSS-Protection
echo "Header set X-XSS-Protection \"1; mode=block\"" >> /etc/apache2/apache2.conf
/usr/sbin/apache2ctl -D FOREGROUND
It can be done with :
- Browser: Azure Portal => App Service => Development Tools => SSH =>
vi /home/site/wwwroot/startup.sh&&chmod +x /home/site/wwwroot/startup.sh - Traditional FTP Client
Step2 - Configure App Service Startup Command
Go to Configuration tab => General settings and update startup command:
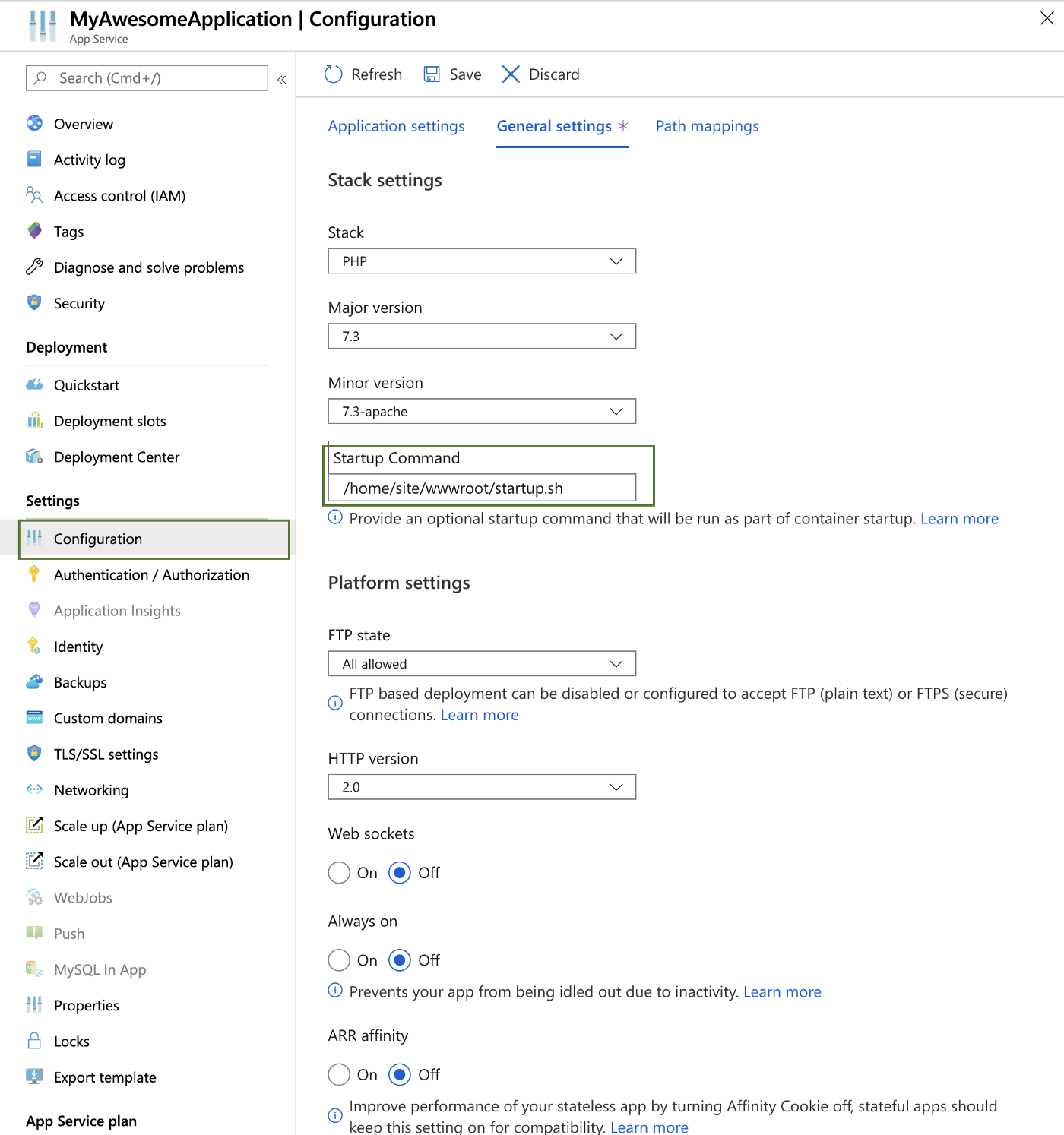
Step3 - Restart
From Overview tab, Restart App Service and check logs using “App Service Logs” tab.
Step4 - Test
Check the result:
- Using securityheaders.io
- Old school:
curl --head https://myawesomesite.com
Source
This blog post is widely copied from the below articles:
